-
BIG_IP SSL Orchestrator
-
More

資料處理中, 請稍候...
Loading...
Visualize SSL/TLS encrypted traffic, assist in in-depth inspection of information security devices, and improve overall protection capabilities.

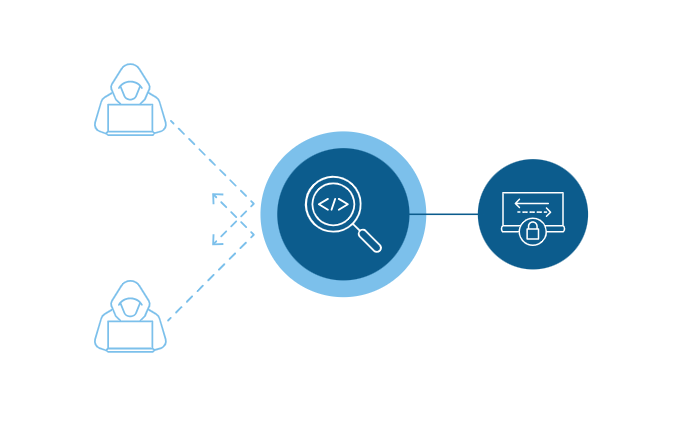
Protect against encrypted threats Bad actors take advantage of SSL/TLS encryption to hide malicious payloads to outsmart and bypass security controls. Don’t leave your organization vulnerable to attack with security solutions that can’t inspect encrypted traffic efficiently at scale. BIG-IP SSL Orchestrator delivers high-performance decryption of inbound and outbound SSL/TLS traffic, enabling security inspection that exposes threats and stops attacks before they happen.
|  |
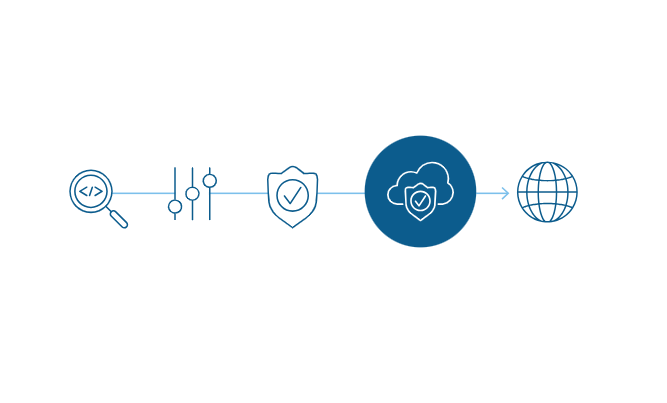 | Intelligently manage encrypted traffic You need orchestration to be on top of your security game. Visibility into and inspection of SSL/TLS traffic is a start, but it only scratches the surface. Daisy-chaining or manually configuring security solutions to support inspection across your security stack’s not scalable and ineffective. BIG-IP SSL Orchestrator intelligently manages the decrypted traffic flow across your entire security stack.
|
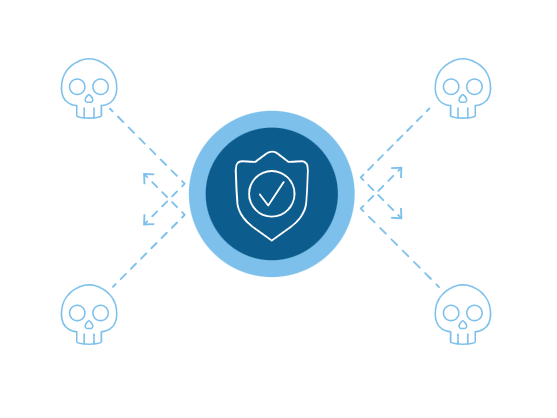
Mitigate ransomware Ransomware is one of the fastest growing cybersecurity threats. What once was an uncommon threat now makes up almost half of all attacks. Unfortunately, ransomware shows no signs of slowing down. It’s critical you protect your organization from ransomware sneaking in through encrypted payloads. BIG-IP SSL Orchestrator maximizes your ability to block these attacks by creating a comprehensive ransomware defense.
|  |
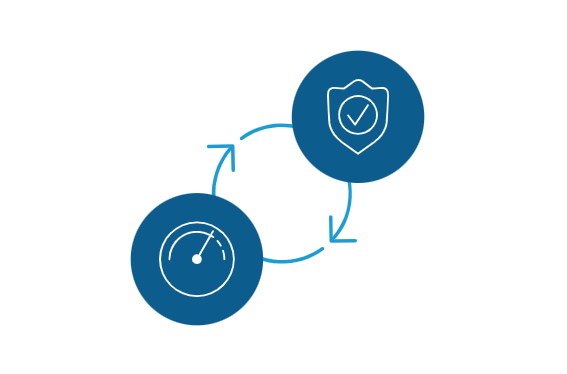 | Simplify security change management The time involved in swapping out, upgrading, or changing a solution in your security stack increases your operational and business costs—and can be dangerous. Daisy-chained security stacks can lead to lengthy delays in making security changes that your business needs now. BIG-IP SSL Orchestrator delivers dynamic security orchestration that drives security changes at the speed of your business.
|
Product Overview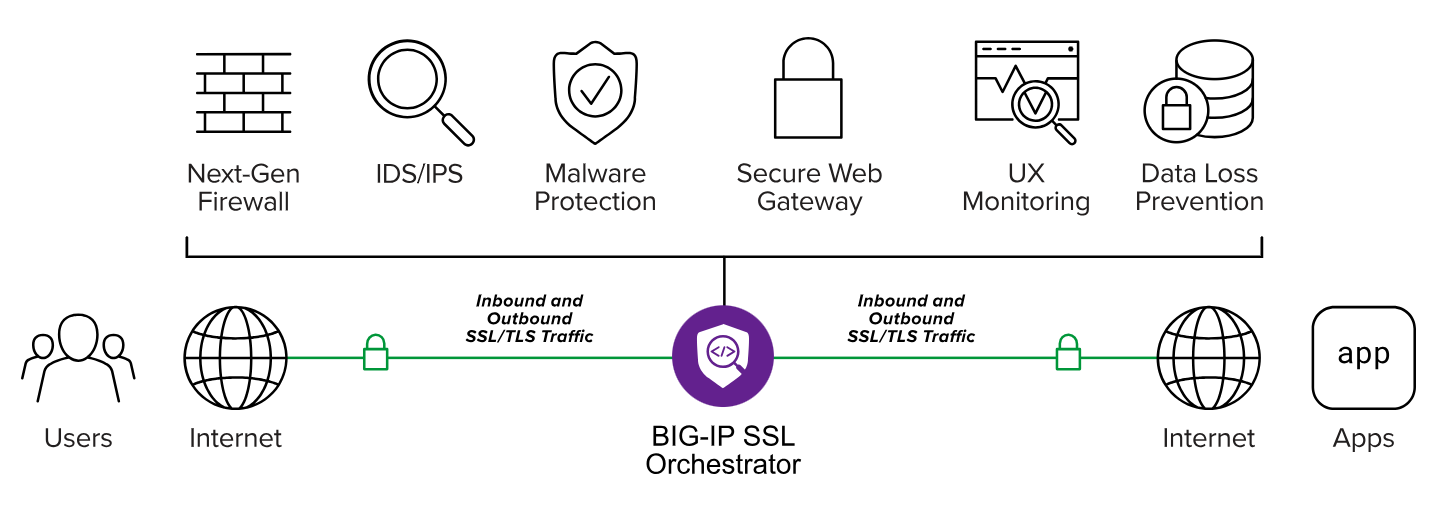 | |
F5 dynamic traffic steeringBIG-IP SSL Orchestrator enhances SSL/TLS infrastructure, makes encrypted traffic visible to security solutions, and optimizes existing security investments. It delivers dynamic service chaining and policy-based traffic steering—applying context-based intelligence to encrypted traffic handling to intelligently manage the flow of encrypted traffic across the security stack—and ensures optimal availability and security. | |
HardwareDeploy high-performance hardware in your on-premises data center or collocation facility. | Software (virtual edition)Deploy on any hypervisor within your data center, collocation facility, or in AWS, Azure, or Google Cloud. |
Core CapabilitiesIf you’re not inspecting SSL/TLS traffic, you’ll miss attacks and leave your organization vulnerable. BIG-IP SSL Orchestrator provides robust decryption/re-encryption and orchestration of encrypted traffic. 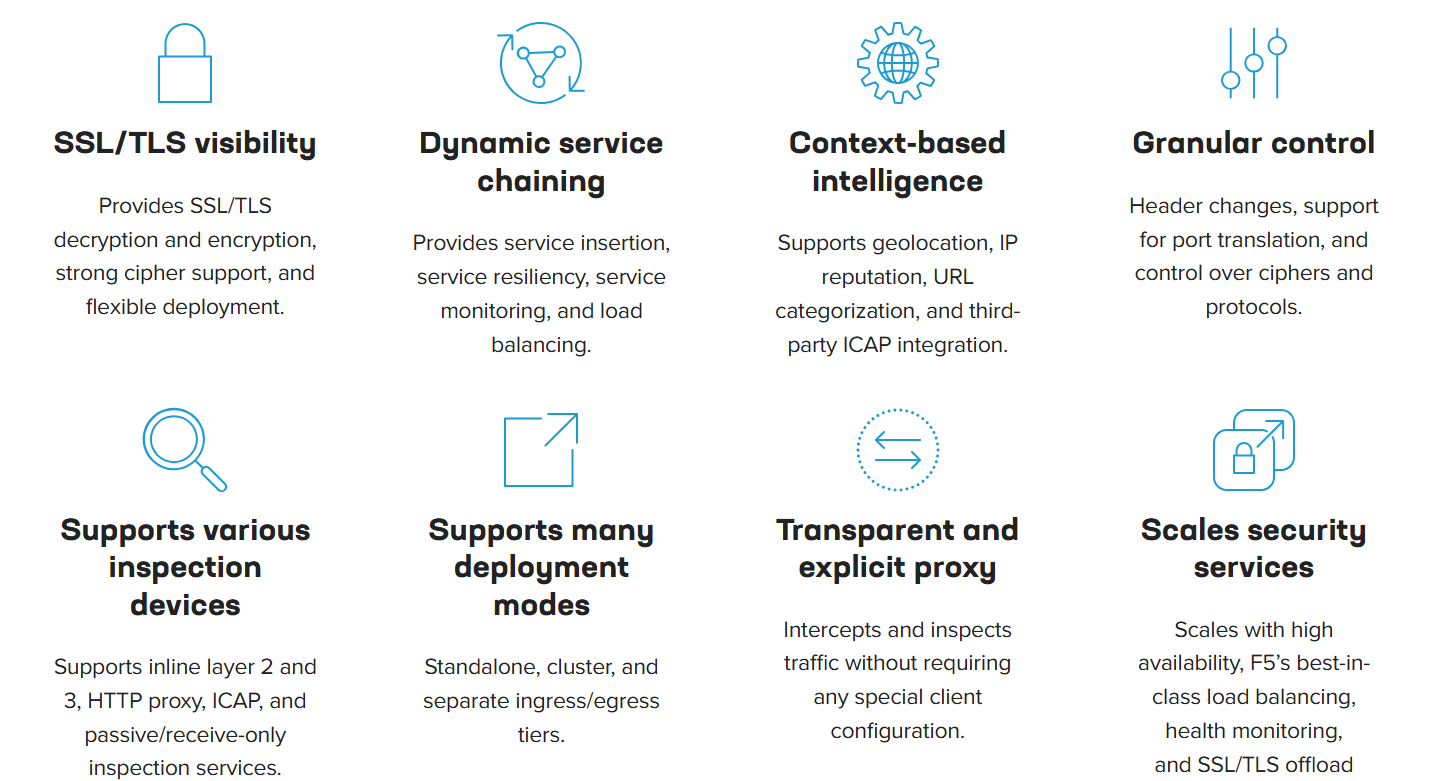 | |
 Service Hotline
Service Hotline
Customer service hours 9:00 - 18:00
 Contact Email
Contact Email
Send your valuable comments by E-mail